The process to regenerate new certificates is:
- Update the server certificate.
- Update each AFX Server client certificate.
- Update each remote collection agent client certificate (if you use remote agents.)
NOTES:
- AFX and remote agents will not be running until this entire process is completed. Therefore, do this at a time when the system is quiet.
- The server certificate (first step) does not always need to be regenerated. Sometimes just downloading the server and client keystores is sufficient as long as their fingerprints match. Sometimes only the client certificate needs to be regenerated. Once regenerated, both the server and client keystores may be downloaded and their fingerprints checked. The complete process is to regenerate both the server and client keystores and that is what article describes.
Update the server certificate
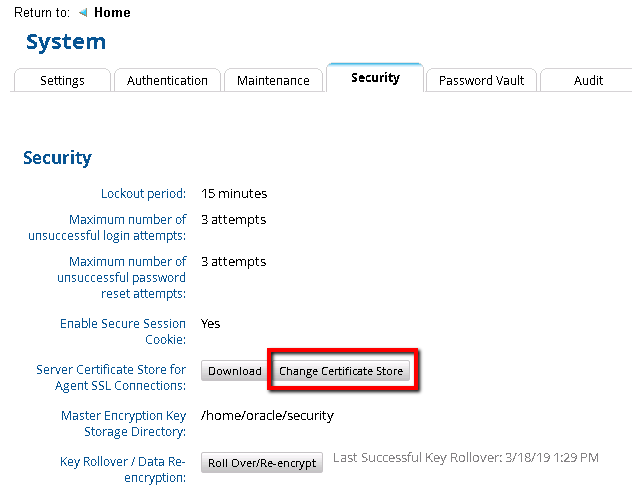
- In the RSA Identity Governance & Lifecycle user interface go to Admin > System > Security tab.
- Under Server Certificate Store for Agent SSL Connections: click the Change Certificate Store button.
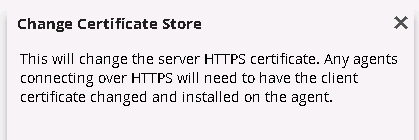
You will see the following dialog message. Click OK to generate the new server certificate.
- Click the Download button and save the server.keystore to a location on your computer.
- Login to the application server as the oracle user.
- Download the new server.keystore to your RSA Identity Governance & Lifecycle application server. In this example the keystore file was downloaded to $AVEKSA_HOME (/home/oracle).
- Go to the keystore directory
cd $AVEKSA_HOME/keystore
- Backup the existing server.keystore.
mv server.keystore server.keystore.bak
- Replace the existing server.keystore with the new server.keystore file that was just downloaded.
mv $AVEKSA_HOME/server.keystore $AVEKSA_HOME/keystore
- Restart RSA Identity Governance & Lifecycle.
acm restart
Update each AFX Server client certificate
Update the AFX server client certificate for each AFX Server by updating the client.keystore and restarting the AFX and RSA Identity Governance & Lifecycle applications.
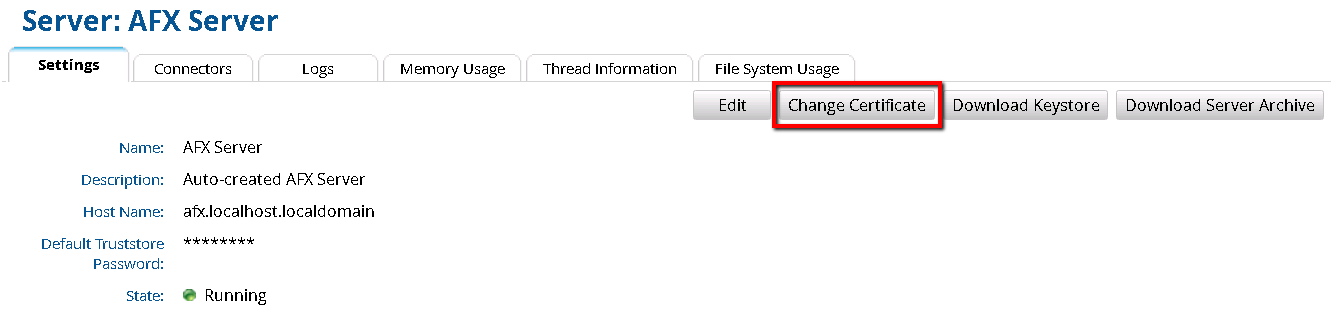
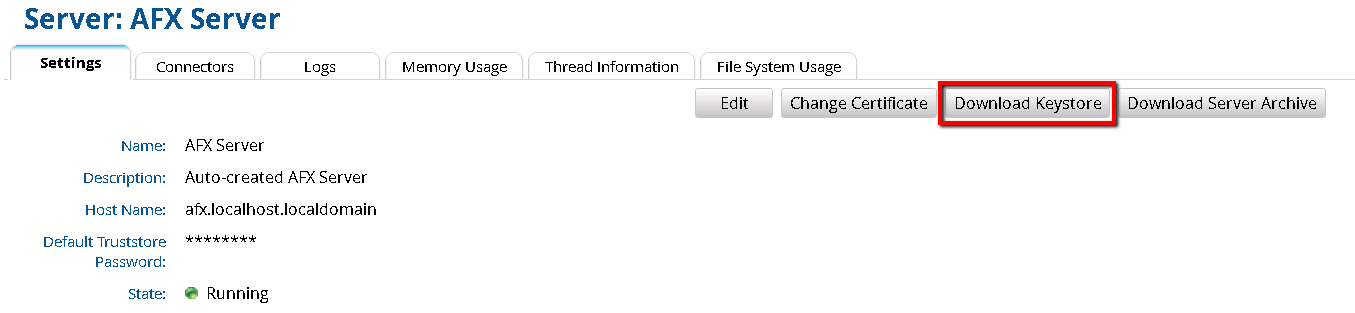
- In the RSA Identity Governance & Lifecycle user interface go to AFX > Servers.
- For each AFX Server, click on the AFX Server name.
- Click the Change Certificate button. This action generates a new client certificate based off the new server certificate just generated and ensures the client certificate stored in the database matches the server certificate stored in the database.
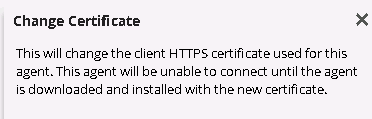
You will see the following dialog message. Click OK to generate the new client certificate.
- Click the Download Keystore button and save the client.keystore to a location on your computer.
- Login to the application server where AFX is installed as the afx user.
- Download the new client.keystore to your RSA Identity Governance & Lifecycle AFX server. In this example the keystore file was downloaded to $AVEKSA_HOME (/home/oracle).
- Go to the keystore directory.
cd $AFX_HOME/esb/conf
- Backup the existing client.keystore.
mv client.keystore client.keystore.bak
- Replace the existing client.keystore with the new client.keystore file that was just downloaded.
mv $AVEKSA_HOME/client.keystore $AFX_HOME/esb/conf
- Restart AFX and the RSA Identity Governance & Lifecycle application.
afx stop
acm restart
afx start
Update each remote collection agent client certificate
- In the RSA Identity Governance & Lifecycle user interface go to Collectors > Agents.
- For each remote agent (not the default local AveksaAgent), click on the remote agent name.
- Click the Change Certificate button. This action generates a new client certificate based off the new server certificate just generated and ensures the client certificate stored in the database matches the server certificate stored in the database.
You will see the following dialog message. Click OK to generate the new server certificate.
- Click the Download Agent button to download a new agent with the new certificate in a zip file called AveksaAgent.zip.
- Login to the remote server that has the remote agent as user oracle.
- Download the new AveksaAgent.zip to the remote server. In this example, the zip file was downloaded to /home/oracle.
- Stop the agent by running agent_stop.sh in the AveksaAgent/bin directory, as follows:
cd home/oracle/AveksaAgent/bin
./agent_stop.sh
- Backup the agent directory.
cd /home/oracle
mv <agent-directory> <agent-directory.bak>
- Unzip the agent on the remote server where it runs (replacing the old one).
unzip AveksaAgent.zip
- Start the agent by running agent_start.sh in the AveksaAgent/bin directory, as follows:
cd home/oracle/AveksaAgent/bin
./agent_start.sh



